Description
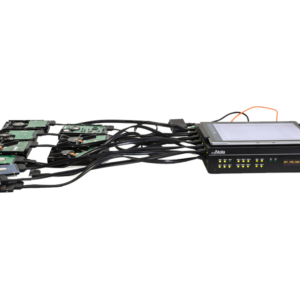
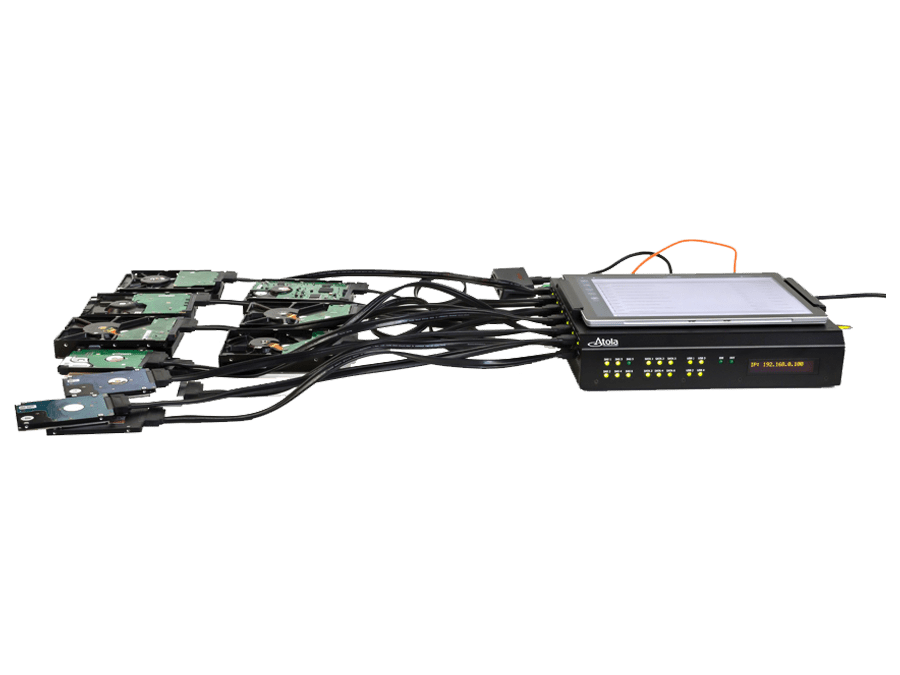
Atola TaskForce is a high-performance forensic imager capable of working with both good and damaged media, developed specifically for forensic use.
It supports SAS, SATA, USB and IDE drives via 18 ports, and other storage devices via Thunderbolt, Apple PCIe, and M.2 SSD extension modules.
TaskForce can be operated either in standalone mode or by multiple users within the same local network.
This forensic imager consists of a hardware unit and software accessible in Google Chrome browser.
TaskForce Web API enables automation of forensic imaging and subsequent start of evidence analysis with software like Magnet AXIOM, X-Ways, Autopsy, etc.
Product Description
12+ simultaneous imaging sessions
Atola TaskForce combines vast multi-tasking capabilities with the fastest imaging engine in the forensic market.
Its server-class hardware enables launching and managing 12+ parallel image acquisition processes.
- 15 TB/hour cumulative speed of imaging
- Imaging to up to 5 targets
- Source/target switch on all ports
- Hardware write protection in Source mode on all ports
- 2 x 10Gb Ethernet ports
- Forensic imaging to E01 and RAW files
- Express mode, in which imaging sessions start the moment a device is connected
- Automation via Web API

Damaged drive support
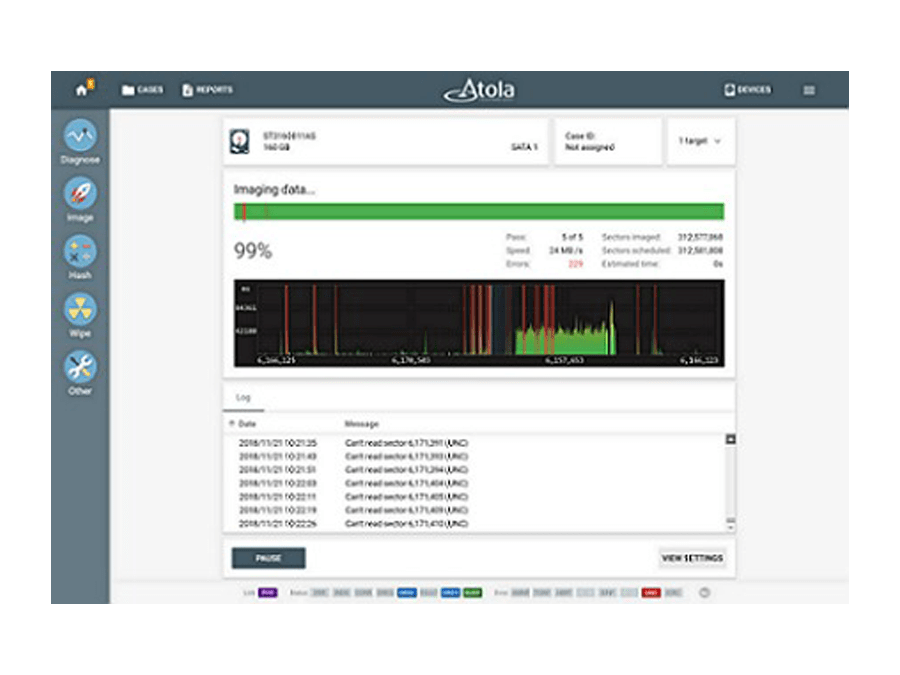
Physically damaged hard drives and problematic solid-state drives require a complex imaging approach. TaskForce forensic imager is designed to achieve the best results getting as much data as possible. It includes the following features:
- Imaging data from good heads only
- Imaging freezing drives
- Imaging drives with surface scratches and firmware issues
- In-depth drive diagnostics
- Current sensor on all SATA, SAS/SATA, IDE ports
- Automatic overcurrent and short-circuit protection
TaskForce hardware is equipped with full circuit protection to prevent a malfunctioning storage device connected to the unit causing damage to the system or to itself.
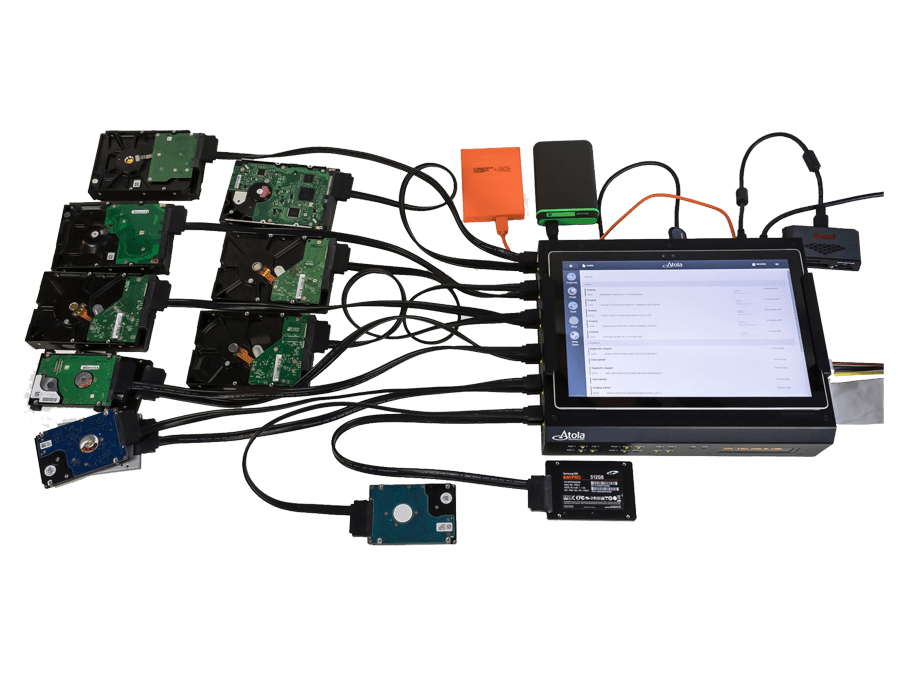
Multi-user access from any device
TaskForce user interface is highly intuitive, task-oriented. It is designed to facilitate work with evidence for investigators with different levels of technical proficiency.
UI features are:
- Operating the unit via Chrome browser
- Simultaneous operation by multiple users
- Launching any operation within a couple of clicks or taps
- Highly intuitive task-oriented user interface

Starting imaging of all available source drives plugged into TaskForce
In this scenario, all 12 of TaskForce’s SATA and SAS ports are switched to Source mode and source drives are plugged into them. TaskForce forensic disk cloning tool instantly launches 12 imaging sessions using Web API.
Python script utilizes /start-image API request and prints task keys of all started imaging sessions.
import sys
if sys.version_info[0] < 3:
raise Exception("Please use Python 3 to run this script")
import urllib.request
ports = ["SATA1", "SATA2", "SATA3", "SATA4", "SATA5", "SATA6", "SAS1", "SAS2", "SAS3", "SAS4", "SAS5", "SAS6"]
tasks = []
errors = {}
for port in ports:
try:
res = urllib.request.urlopen("http://10.0.0.4/api/start-image?source=%s&targetFolder=//Vitaliy/Share" % (port))
tasks.append(res.read().decode('utf-8'))
except urllib.error.HTTPError as e:
errors[port] = e.read()
print("IDs of started imaging tasks:")
print('\n'.join(tasks))
Automatic file analysis upon completion of forensic disk cloning (imaging)
By sending /check-task API requests to TaskForce forensic imager, you can track the status of the running imaging sessions. TaskForce returns a report about the imaging progress allowing you (or your code) to find out when the task is completed. Upon receveing this notification, the automation tool launches the forensic analysis of the target image. The Powershell script below demonstrates how this automation flow can be created:
try {
$r = Invoke-WebRequest "http://10.0.0.65/api/start-image?source=SATA4&targetFolder=\\Vitaliy\Share"
}
catch {
Write-Output "$($_.Exception.Message)"
exit $_.Exception.Response.StatusCode
}
$taskKey = $r.Content
do {
$check = (Invoke-WebRequest "http://10.0.0.65/api/check-task?taskKey=$taskKey").Content | ConvertFrom-Json
Start-Sleep -s 1
} while ($check.state -eq "progress")
$windowsPath = "C:\Share\" + ($check.target -replace '[\/]', '\' | Split-Path -leaf)
$caseName = "Case123"
$autopsyArguments = '--inputPath="' + $windowsPath + '" --caseName=' + $caseName + ' --runFromCommandLine=true'
Start-Process -FilePath "C:\Program Files\Autopsy-4.11.0\bin\autopsy64.exe" -ArgumentList $autopsyArguments
NB. Autopsy Ingest v4.11 does not work with network file paths from the command line. That’s why this example shows a shared folder located at PC where PowerShell script is executed. Therefore \\Vitaliy\Share points to C:\Share folder.