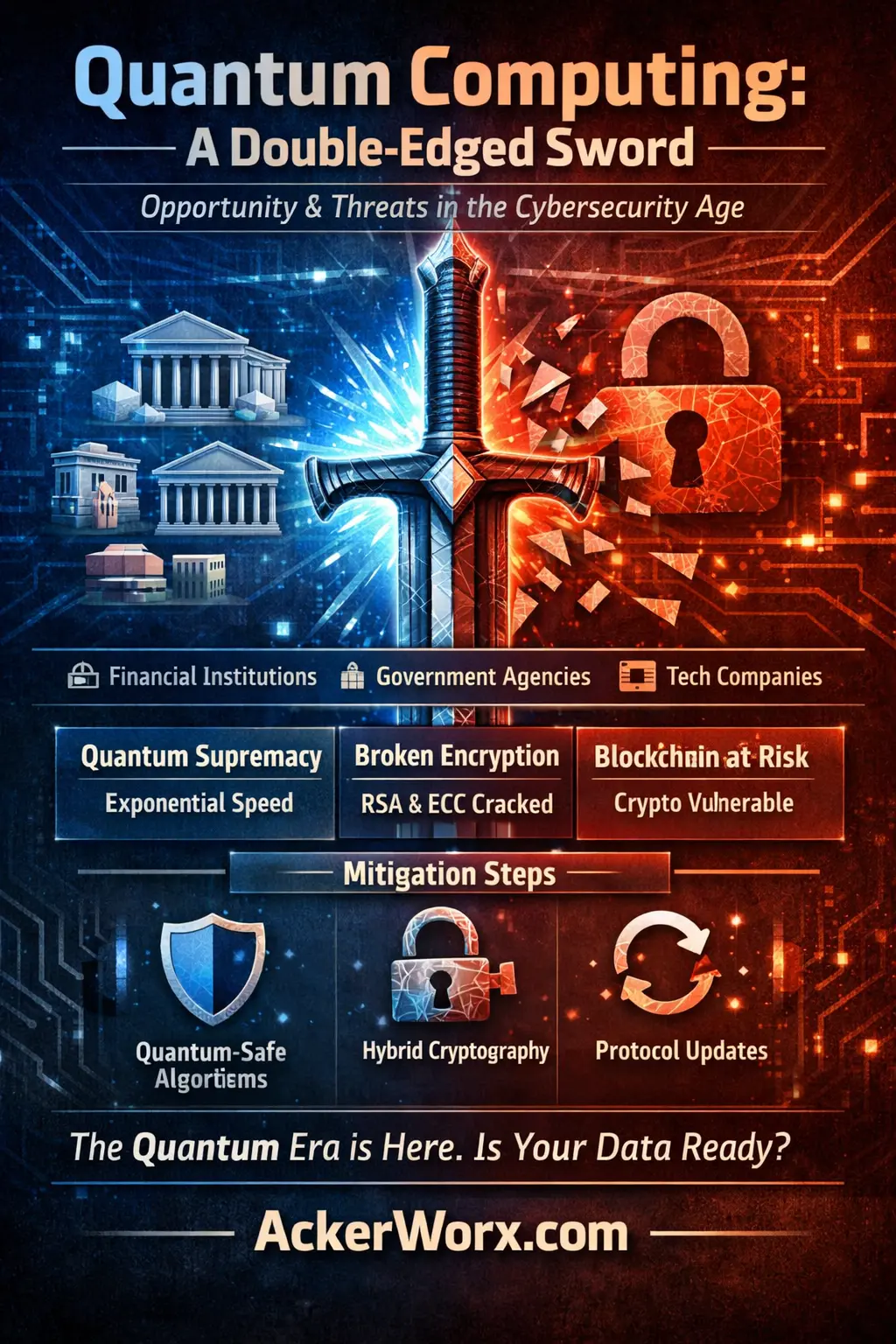
Quantum Leap in Cybersecurity: January 2026 Trends

Autonomous AI Threat Agents: Welcome to the New Cyber Battlefield

Beyond the Firewall: Why Modern Data Breaches Aren't What You Think

Pixnapping (CVE-2025-48561): An Architectural Flaw in Android
How Agentic AI Is Redefining Work in 2025

Quantum-Resilient Cryptography: The Clock Is Ticking on RSA and ECC

🔐 SASE: The Future of Secure Access in a Borderless World

Inside 2025's Biggest Cybersecurity Threats: Hardware-Level Hacks, Firmware Backdoors, and What You’re Not Patching
 Tech Stack
Tech StackWhy AckerWorx Developers Switched from ESLint and Prettier to Biome — A Technical Deep Dive
At AckerWorx, our developers strive for code clarity, maintainability, and efficiency. Like most teams in the JavaScript and TypeScript ecosystem, we've relied heavily on the classic duo: ESLint for...
Read More
Why Ackerworx Pulled Out of the UK: Protecting Encryption and Digital Freedom
March 3, 2025
NoData 2025: The Future of Unbreakable Data Security is Here
March 3, 2025
AckerWorx S22 Ultra: The Ultimate Mobile Penetration Testing Platform
March 1, 2025
Introducing the WORX-5 (2025 Edition): The Next Evolution in Rugged Computing
March 1, 2025
Samsung S22 Ultra Forensics Upgrade
Officially Samsung have no plans to release Android 10/Q on the S8. For those of you out of warranty or wanting a new lease of life for your aging device. Device Performance Unaffected
€ 750,00
RFID Fuzzer
The world's only RFID fuzzing tool. Securely disable RFID badges. Test and harden RFID hardware Audit access control failure modes Test and reduce the attack surface for pen-test customers Single Discharge Mode Continuous Discharge Mode
€ 280,00
AutoPi Telematics Unit - 4G/LTE Edition
This is the 4G/LTE edition of the new AutoPi Telematics Unit which includes a 4G/LTE modem with global support.
€ 300,00
Quantum Leap in Cybersecurity: January 2026 Trends
Quantum computing is redefining January 2026 cybersecurity, threatening RSA and ECC. Organizations must adopt quantum-resistant methods swiftly.
Read More Hot Topic
Hot TopicAutonomous AI Threat Agents: Welcome to the New Cyber Battlefield
Forget hooded hackers at keyboards. In 2026, the most dangerous cyber threat doesn't sleep, doesn't take breaks, and can attack thousands of targets simultaneously. Autonomous AI threat agents are here, and they're changing everything about how we think about defense.
Read More Ackerworx
AckerworxBeyond the Firewall: Why Modern Data Breaches Aren't What You Think
Your company has been breached. It’s the scenario that keeps CISOs and CEOs awake at night. But this isn't a 90s movie where a hacker is "in the mainframe." The breach didn't happen by breaking down...
Read More Ackerworx
AckerworxPixnapping (CVE-2025-48561): An Architectural Flaw in Android
A new, high-severity vulnerability has been disclosed by a team of U.S. university researchers, and its implications go far beyond a typical software bug. Dubbed "Pixnapping," this attack method, now...
Read More
Quantum Leap in Cybersecurity: January 2026 Trends
January 9, 2026
Autonomous AI Threat Agents: Welcome to the New Cyber Battlefield
January 7, 2026
Beyond the Firewall: Why Modern Data Breaches Aren't What You Think
October 30, 2025
Pixnapping (CVE-2025-48561): An Architectural Flaw in Android
October 30, 2025






